Quick Guide to BIND 8 |
|
Introduction
This guide will help you set up a DNS server from scratch. There are currently two version of ISC's BIND server package: BIND 4 and BIND 8. As it's more secure and feature-rich, you should install BIND 8.
Setup
To install BIND, just get the main BIND RPM package, and the BIND-Utils package that contains tools like nslookup.
- rpm -Uvh bind-8.2.2_P5-6.rpm
- rpm -Uvh bind-utils-8.2.2_P5-6.rpm
This will install /etc/named.conf and create an empty /var/named directory where you'll have to create the actual zone files for your domain.
Configuration
/etc/named.conf
- options {
directory "/var/named";
pid-file "named.pid";
allow-query { localnets; };
allow-transfer { 10.0.1.15;
}; };
- zone "." { type hint; file "db.cache"; };
- zone "localhost" { type master; file "localhost.zone"; };
- zone "0.0.127.in-addr.arpa" { type master; file "db.127.0.0"; };
- zone "acme" { type master; file "db.acme"; allow-update {none; }; };
- zone "0.168.192.in-addr.arpa" { type master; file "db.192.168.0"; allow-update {none; }; };
- zone "." { type hint; file "db.cache"; };
/var/named/db.acme
|
$TTL |
1D |
|
|
|
|
@ |
SOA |
linux |
root |
(2001091601 3H 1H 1W 1D) |
|
|
NS |
linux |
|
|
|
|
MX |
10 |
linux |
|
|
|
CNAME |
linux |
|
|
|
linux |
A |
192.168.0.1 |
|
|
|
ftp |
CNAME |
linux |
|
|
|
www |
CNAME |
linux |
|
|
|
fred |
A |
192.168.0.2 |
|
|
Note: The first CNAME record (CNAME linux) allows the user to reach the linux host by just querying "acme". It's useful to allow the web server to be reached with just "http://acme" instead of "http://linux.acme". Also, do remember the brackets to enclose the numerical parameters for the SOA record.
Important: In the email address of the contact for the zone in the SOA record ("root", here), if the user name contains a dot, it must be escaped, with \ ; Otherwise, BIND will think it is the beginning of the domain name, and will turn this dot into @. For instance, if the admin email address is john.doe, the SOA must say john\.doe.acme.com .
/var/named/db.192.168.0
Note that all hostnames in reverse files must be FQDN, or BIND will gladly append the zone name...|
$TTL |
1D |
|
|
|
|
@ |
SOA |
linux.acme. |
root.acme. |
(2001091601 3H 1H 1W 1D) |
|
|
NS |
linux.acme. |
|
|
|
1 |
PTR |
linux.acme. |
|
|
|
2 |
PTR |
fred.acme. |
|
|
/var/named/db.localhost
|
$TTL |
1D |
|
|
|
|
@ |
SOA |
localhost. |
root |
(2001091601 3H 1H 1W 1D) |
|
|
NS |
localhost. |
|
|
|
|
A |
127.0.0.1 |
|
|
/var/named/db.127.0.0
|
$TTL |
1D |
|
|
|
|
@ |
SOA |
localhost. |
root |
(2001091601 3H 1H 1W 1D) |
|
|
NS |
localhost. |
|
|
|
1 |
PTR |
localhost. |
|
|
/var/named/db.cache
|
. |
NS |
A.ROOT-SERVERS.NET. |
|
A.ROOT-SERVERS.NET. |
A |
198.41.0.4 |
|
. |
NS |
B.ROOT-SERVERS.NET. |
| B.ROOT-SERVERS.NET. |
A |
128.9.0.107 |
|
. |
NS |
C.ROOT-SERVERS.NET. |
| C.ROOT-SERVERS.NET. |
A |
192.33.4.12 |
|
. |
NS |
D.ROOT-SERVERS.NET. |
| D.ROOT-SERVERS.NET. |
A |
128.8.10.90 |
|
. |
NS |
E.ROOT-SERVERS.NET. |
| E.ROOT-SERVERS.NET. |
A |
etc. |
Notes
- In reverse lookup files, all hostnames must be qualified and end with a "."
- It's actually possible to keep all records in a single file. All hostnames must be fully-qualified since you can no longer rely on the Origin to complete hostnames.
- Nslookup is being deprecated. Instead, use "host mylinux", "host -t mx acme", or
Records
- $TTL 1D
- @ SOA linux root 1984081201 3H 1H 1W
- @ MX 10 linux
- @ NS linux
- @ A 192.168.0.1
- localhost A 127.0.0.1
- linux CNAME @
- ftp CNAME @
- mail CNAME @
- www CNAME @
- news CNAME @
- ldap CNAME @
- radius CNAME @
- fred A 192.168.0.2
- @ SOA linux root 1984081201 3H 1H 1W
The @ sign is a short-hand for the name of the zone. If you use this instead of spelling it out, BIND checks /etc/named.conf to find out which zone this file defines. The domain name is appended to any host not ending with a ".", ie. hosts that are not fully-qualified.
SOA record
This is the most important record, and indicates that this file is authoritative for this zone. In the SOA record above, the first number (1984081201, here) is a serial number that you must increase every time you change anything in your zone files so that secondary servers can tell that something has changed. Making a change but forgetting to update this serial number is a common error, and results in secondary servers not downloading the new zone files.The seconde number (3H) is the Refresh period, which tells secondaries how long they should wait until contacting the primary and check whether its zone files have changed.
The third number (1H) is the Retry number. It tells secondaries how often it should try contacting the primary once the Refresh period is up but the primary is not answering queries.
The last number (1W) is the Expire number. Once this time is up, secondaries will flush their data, and no longer resolve names for that zone. It is thought a better idea not to answer than to return stale data.
(CHECK) According to the book on DNS published at Craig Hunt, the optional default TTL that is included in the SOA is actually the negative cache, ie. the amount of time a DNS server should remember that a host could not be resolved the last time its IP address was queried.
Other records
;========================= MX
; To let you use jdoe@acme.com instead of jdoe@linux.acme.com
MX 10 linux
;========================= NS
;Name servers authoritative for that zone.
;Should match what it says in your NIC record when you registered your domain
NS linux
;========================= The Whole Shebbang
; Used so you can just type eg. http://acme.com instead of www.acme.com
@ A 192.168.0.1
localhost A 127.0.0.1
linux CNAME @
ftp CNAME @
mail CNAME @
www CNAME @
news CNAME @
ldap CNAME @
radius CNAME @
fred A 192.168.0.2
metoo CNAME fred
The PTR records ("pointer") go into the reverse zone file:2 PTR fred
Tips & Tricks
Querying BIND
As nslookup is being deprecated, you should use dig or host to query BIND.
dig
- dig mylinux.acme.
- dig -x 192.168.0.1
- dig soa acme
- dig mx acme
host
- host -t mx acme
- host mylinux
Hiding the version number
- From: "Cricket Liu" <cricket@nxdomain.com>
- Newsgroups: comp.protocols.dns.bind
- Subject: Re: not revealing version number at all
- Date: 18 Jul 2001 09:27:34 -0700
- I know that one can set the option "version" to make the version number of your server that is returned by dig something ludicrous. I recently came
- across a server that does not give a version number at all -- the status is "REFUSED". I don't see in the doc a way to not respond to a version query
- at all. I have two questions for the collective: do people think this is a good idea or not, and secondly how is this done (since I do not find it in the doc).
- You could use the old technique of setting up CHAOSNET "bind" zone and use allow-query to prevent folks from querying it, e.g.,
- zone "bind" ch {
- type master;
- file "db.bind";
- allow-query { none; };
- };
- db.bind would just need an SOA record and an NS record.
- From: dns_web2000@yahoo.com (Mark Thompson)
- Under options:
- options {version "REFUSED"; };
- Newsgroups: comp.protocols.dns.bind
After making any change to your zone files, tell named to re-read its files through either killall -HUP named or /etc/rc.d/init.d/named restart, and run DnsWalk. Dnswalk is a Perl script that will connect to your DNS server, perform a zone transfer, and look for errors.
You can also add TXT records, which hand out information about hosts, but it is not recommended to give away more information about your site than is strictly necessary. The less hackers know about your network, the better.
Updating the root cache file
- ftp rs.internic.net
- cd domain
- mget named.root
- mv named.root /var/named/db.cache
Things to watch out for
- Missing "." at the end of a line, causing BIND to add your domain name to the host. For instance, myhost.acme.com ends up as myhost.acme.com.acme.com
- Making changes to zone files without increasing the serial number. Secondaries will not transfer the zones.
- (BIND 8 ONLY?) Empty lines. If you want to add comments or spaces for increased readibility, either use ; (recommended), or add at least a single space on the line (not recommended; It took me quite a while once to find that one...)
- Using aliased hostnames instead of real hostnames for the NS records. Aliased = CNAME hosts; Real = A hosts
Setting up a DNS server in a private/public network
The goal here is to set up DNS for your Internet-connected network, and answer queries from either the Internet or hosts in your private network.There are two issues: Where to locate the DNS server itself, and what information to put in its zone files.
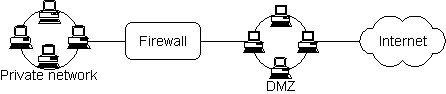
As suggested by Erik Jan van Westen in the comp.os.linux.networking newsgroup, here are the different possibilities:
- Set up two DNS servers, one in the DMZ to answer queries from the Internet, and one in the private network to answer queries from your corporate sites.
The zone file on the DNS in the public network contains only hosts that you want to make accessible from the Internet, eg. your DNS (obviously), you mailer, your public Web server, FTP server, etc.
The zone file on the DNS in the private network contains only corporate hosts. This zone file contains only private, non-routable IP addresses (ie. 10.x.x.x, 172.16-31.x.x, 192.168.x.x addresses.)The zone in the public network should obviously be the one that was registered to the NIC, eg. acme.com. Use a fake zone in your private zone to enhance security and also to forward queries to your public DNS server for public hosts. To avoid choosing a domain name that is already in use somewhere on the Internet, pick a domain name which is very unlikely to be ever used (eg. dummy.zzz).
As a practical example, if you only want to use one mailer for both Internet e-mail and corporate e-mails, and you use acme.com as your public zone and dummy.zzz as your private zone: Mail clients in your private network should be set up to use @acme.com for all corporate e-mails. Set up our private DNS to forward all queries that it cannot answer to your public DNS server.
That way, corporate e-mails are indeed sent to your mailer in the DMZ: If I'm sending e-mail to jdoe@acme.com, our private DNS server only handles the dummy.zzz zone. Since it knows nothing about zones other than dummy.zzz, the private DNS server forwards queries to the public DNS server, which is authoritative for the acme.com zone. Since mails meant for @acme.com do not specify the actual mailer, the public DNS server returns the MX record for the dummy.com zone, which is the address of the mailer sitting in the DMZ.
E-mails coming from the Internet and meant for the @acme.com zone are resolved directly by querying our public DNS server, in the DMZ.
Needless to say, you should not advertise the dummy.zzz zone since it has no existence outside of your private, corporate network. You might want to set up domain masquerading on your mailer to hide this piece of information.
- Set up one DNS server, so you only need to handle one zone file. This single DNS can be either located in the DMZ, on the firewall, or in the private network.
Solution #1: I don't recommend it be put on the firewall. Security-wise, I'd rather keep the firewall as simple as possible, which is also the reason why I recommend you use a hardware-based firewall instead of a computer running NT or *nix.
Solution #2:Another suggestion by Erik was to use two NICs on the DNS server, have it run two instances of BIND, each using a different version of your zone file: The instance listening to the NIC connected to your DMZ uses the public version of your zone file, while the NIC that listens to requests from your private network uses the private version of your zone file. Since you already have a firewall to filter data flowing between your two networks, I wouldn't recommend adding a second gate that is this DNS.
Solution #3: The easiest way is to set up your public servers in the DMZ, and use only one zone, to be used both by public hosts in the DMZ and private hosts in the private network (ie. all hosts should be registered in the acme.com zone file.) By "public servers", I mean those that must be reached by both Internet hosts and private hosts. That way, the DNS can return a valid, public address whether the query came from the Internet or your private network. To use the example of e-mail, the MX record contains the public address of our mailer in the DMZ. That way, both Internet hosts and private hosts can reach our mailer directly.
A variation of this setup is to put all your servers, including those advertised on the Internet, in the private network, ie. with no host in the DMZ. Our single DNS server in the private network answers queries from both the Internet and the private corporate network, and the firewall is set up to use static mapping so that servers can be reached from the Internet through the firewall.
The issue here, is that BIND should return a different address depending on where the query came from: To get back to the MX example, if an Internet mailer needs to send e-mail to you, the MX record should return the mailer's public static IP address (obviously, returning eg. 10.0.0.1 as your mailer address makes no sense to an Internet host.) But if the query came from your private network, the MX record should return the private address of our mailer since it is now sitting in the private network.
Although I haven't looked into this yet, Erik says that BIND version 9 is supposed to be able to return a different address depending on where the query came from (without using the two-NIC setup explained above): In the example above, BIND 9 will return the mailer's public IP address if the query came from the Internet, but it will return the mailer's private IP address if the query came from your private network.
Reverse-lookup zone file for subnets
In case your ISP granted you a network number which doesn't fall neatly on a byte-boundary (eg. netmask of 255.255.255.192), the reverse lookup zone file needs to be twicked a little.Resources
DNS & BIND
Read the classic "DNS & BIND" from O'Reilly, but note that BIND 8 wasn't available at the time of its writing, so it only deals with BIND 4.DNSWalk
A Perl script that performs a zone tranfer and parses your zone files for errors. Very impressive.WebMin
This is a cool web-based application that offers modules to manage the different daemons sitting on a server, eg. DHCPd, BIND, Postfix, etc.Nslookup
The first utility that you should use to check that your DNS server is set up correctly. It connects to the server and lets you resolve names or get records.To find a host's IP address, nslookup ahost (or ahost.acme.com if it resides in a domain that is different from what you specified in /etc/resolve.conf)
To find a host's hostname from its IP addres, nslookup 192.168.1.1
To perform lookups on a different DNS server that the first server specified in /etc/resolve.conf, nslookup ahost.acme.com dns.isp.com
To check a given record, nslookup, followed by set type=soa/mx/a/all, followed by the domain name.
Ask Mr DNS: http://www.acmebw.com/askmrdns/
Temp stuff
logging {
category lame-servers { null; };
category cname { null; };
};
controls {
inet * port 52 allow { localnets; }; // a BAD idea
unix "/var/run/ndc" perm 0600 owner 0 group 0; // the default
};
zone domain_name [ ( in | hs | hesiod | chaos ) ] {
type master;
[ forward ( only | first ); ]
[ forwarders { [ ip_addr ; [ ip_addr ; ... ] ] }; ]
[ check-names ( warn | fail | ignore ); ]
[ allow-update { address_match_list }; ]
[ allow-query { address_match_list }; ]
[ allow-transfer { address_match_list }; ]
[ dialup yes_or_no; ]
[ notify yes_or_no; ]
[ also-notify { ip_addr; [ ip_addr; ... ] };
[ ixfr-base path_name; ]
[ pubkey number number number string; ]
};
stub
A stub zone is like a slave zone, except that it replicates only the NS records of a master zone instead of the entire zone.
forward
A forward zone is used to direct all queries in it to other servers. The specification of options in such a zone will override any global options declared in the options statement.
If either no forwarders statement is present in the zone or an empty list for forwarders is given, no forwarding will be done for the zone, cancelling the effects of any forwarders in the options statement. Thus if you want to use this type of zone to change the behavior of the global forward option, and not the servers used, you also need to respecify the global forwarders.
BIND Configuration File Guide -- options Statement
Syntax
options {
[ version version_string; ]
[ directory path_name; ]
[ named-xfer path_name; ]
[ dump-file path_name; ]
[ memstatistics-file path_name; ]
[ pid-file path_name; ]
[ statistics-file path_name; ]
[ auth-nxdomain yes_or_no; ]
[ deallocate-on-exit yes_or_no; ]
[ dialup yes_or_no; ]
[ fake-iquery yes_or_no; ]
[ fetch-glue yes_or_no; ]
[ has-old-clients yes_or_no; ]
[ host-statistics yes_or_no; ]
[ multiple-cnames yes_or_no; ]
[ notify yes_or_no; ]
[ recursion yes_or_no; ]
[ rfc2308-type1 yes_or_no; ]
[ use-id-pool yes_or_no; ]
[ treat-cr-as-space yes_or_no; ]
[ also-notify { ip_addr; [ ip_addr; ... ] };
[ forward ( only | first ); ]
[ forwarders { [ in_addr ; [ in_addr ; ... ] ] }; ]
[ check-names ( master | slave | response ) ( warn | fail | ignore); ]
[ allow-query { address_match_list }; ]
[ allow-transfer { address_match_list }; ]
[ allow-recursion { address_match_list }; ]
[ blackhole { address_match_list }; ]
[ listen-on [ port ip_port ] { address_match_list }; ]
[ query-source [ address ( ip_addr | * ) ] [ port ( ip_port | * ) ] ; ]
[ lame-ttl number; ]
[ max-transfer-time-in number; ]
[ max-ncache-ttl number; ]
[ min-roots number; ]
[ serial-queries number; ]
[ transfer-format ( one-answer | many-answers ); ]
[ transfers-in number; ]
[ transfers-out number; ]
[ transfers-per-ns number; ]
[ transfer-source ip_addr; ]
[ maintain-ixfr-base yes_or_no; ]
[ max-ixfr-log-size number; ]
[ coresize size_spec ; ]
[ datasize size_spec ; ]
[ files size_spec ; ]
[ stacksize size_spec ; ]
[ cleaning-interval number; ]
[ heartbeat-interval number; ]
[ interface-interval number; ]
[ statistics-interval number; ]
[ topology { address_match_list }; ]
[ sortlist { address_match_list }; ]
[ rrset-order { order_spec ; [ order_spec ; ... ] ] };
};
Definition and Usage
The options statement sets up global options to be used by BIND. This statement may appear at only once in a configuration file; if more than one occurrence is found, the first occurrence determines the actual options used, and a warning will be generated. If there is no options statement, an options block with each option set to its default will be used.
version
The version the server should report via the ndc command or via a query of name version.bind in class chaos. The default is the real version number of the server, but some server operators prefer the string "surely you must be joking".
recursion
If yes, and a DNS query requests recursion, the server will attempt to do all the work required to answer the query. If recursion is not on, the server will return a referral to the client if it doesn't know the answer. The default is yes.
also-notify
Defines a global list of IP addresses that also get sent NOTIFY messages whenever a fresh copy of the zone is loaded.
forward
This option is only meaningful if the forwarders list is not empty. A value of first, the default, causes the server to query the forwarders first, and if that doesn't answer the question the server will then look for the answer itself. If only is specified, the server will only query the forwarders.
forwarders
Specifies the IP addresses to be used for forwarding. The default is the empty list (no forwarding).
allow-query
Specifies which hosts are allowed to ask ordinary questions. allow-query may also be specified in the zone statement, in which case it overrides the options allow-query statement. If not specified, the default is to allow queries from all hosts.
allow-transfer
Specifies which hosts are allowed to receive zone transfers from the server. allow-transfer may also be specified in the zone statement, in which case it overrides the options allow-transfer statement. If not specified, the default is to allow transfers from all hosts.
allow-recursion
Specifies which hosts are allowed to make recursive queries through this server. If not specified, the default is to allow recursive queries from all hosts.
blackhole
Specifies a list of addresses that the server will not accept queries from or use to resolve a query. Queries from these addresses will not be responded to.
Query Address
If the server doesn't know the answer to a question, it will query other nameservers. query-source specifies the address and port used for such queries. If address is * or is omitted, a wildcard IP address (INADDR_ANY) will be used. If port is * or is omitted, a random unprivileged port will be used. The default is
query-source address * port *;
Note: query-source currently applies only to UDP queries; TCP queries always use a wildcard IP address and a random unprivileged port.
FF: Can be used on the private DNS to query public DNS for hosts in the DMZ to avoid including public hosts in the private zone file ? (eg. mailer in DMZ)
The controls statement declares control channels to be used by system administrators to affect the operation of the local name server. These control channels are used by the ndc utility to send commands to and retrieve non-DNS results from a name server.
The following ACLs are built-in:
any
Allows all hosts.
none
Denies all hosts.
localhost
Allows the IP addresses of all interfaces on the system.
localnets
Allows any host on a network for which the system has an interface.
Root Hints Files
If your network is not connected to the Internet, you must replace the NS and A records in the cache file with NS and A records for the DNS servers that are authoritative for the root of your private TCP/IP network.
For example, suppose you have created two internal root DNS servers (InternalRoot1.reskit.com. and InternalRoot2.reskit.com.). You then create a root hints file on other DNS servers in your network, pointing to the internal root DNS servers. That way, if other name servers receive a query they cannot resolve, they can simply query the internal root servers specified in the file.
The following reskit root hints file provides NS resource records and name-to-IP address mappings for name servers in the reskit.com domain.
; Internal root hints file for reskit.com, which is not connected to
; the Internet
. 86400 IN NS InternalRoot1.reskit.com.
. 86400 IN NS InternalRoot2.reskit.com.
InternalRoot1.reskit.com. 86400 IN NS 172.16.64.1
InternalRoot2.reskit.com. 86400 IN NS 172.16.64.2
Note
The Windows 2000 Configure DNS Server wizard makes a best effort to determine whether the network is connected to the Internet and, if not, creates its own cache file.
BIND version 9 is a major rewrite of nearly all aspects of the
underlying BIND architecture. Some of the important features of
BIND 9 are:
- Views
One server process can provide multiple "views" of
the DNS namespace, e.g. an "inside" view to certain
clients, and an "outside" view to others.
4.3 Split DNS
Setting up different views, or visibility, of DNS space to internal and external resolvers is usually referred to as a Split DNS setup. There are several reasons an organization would want to set up its DNS this way.
I want to set up DNS on a (closed) intranet. What do I do?
You drop the root.hints file and just do zone files. That also means you don't have to get new hint files all the time.
Resources
- Transactional Security in BIND 9
- Free DNS server on the Net: granitecanyon.com, secondary.com,
- Dynamic DNS Services
- DNS Made Easy
- Dynamic DNS Primer
- In a DNS bind? Get Out with dnsmasq By Carla Schroder
- nsupdate: Quick and Painless Dynamic DNS, Painless DDNS part 2: configuring the server
- Traditional DNS Howto by Tom Adelstein
- Two-in-one DNS server with BIND9 by pupeno
- Alternatives to BIND: PowerDNS, NSD, MaraDNS, Dnsmasq, djbdns,